Google named a Visionary in the 2024 Gartner Magic Quadrant for SIEM. Get your complimentary report.
Google Security Operations
The intelligence-driven and AI-powered security operations platform
Google Security Operations is a modern, cloud-native SecOps platform that empowers security teams to better defend against today’s and tomorrow’s threats.
Features
Detect threats with confidence
Leverage Google curated detections to find the latest threats and map them to MITRE ATT&CK.
Simplify detection authoring with YARA-L to build custom content.
Automatically surface and prioritize findings with access to rich context about threat actors and campaigns from applied threat intelligence.
Identify potentially exploitable entry points accessible to attackers and prioritize remediation with attack surface management integration.
Investigate with insights at your fingertips
Analyze real-time activity with investigation views, visualizations, threat intel insights, and user aliasing.
Investigate with full context at your fingertips, including anomalous assets and domain prevalence and more.
"Google search" petabytes of data at lightning speed.
Manage, prioritize, and assign work with unique threat-centric case management.
Seamlessly pivot between cases, alerts, entities, and detections with a unified experience across the entire TDIR workflow.
Respond with speed and precision
Drive consistency in your response and automate repetitive tasks with a full-featured intuitive playbook builder and 300+ integrations.
Easily collaborate on every case with fellow analysts, service providers, and other stakeholders.
Turn intelligence into action with applied threat intelligence
Leverage intelligence from Google, Mandiant and VirusTotal to automatically uncover potential threats.
Get early warning signals of potential active breaches based on Mandiant’s frontline intelligence.
Continuously analyze twelve months of hot data against the wealth of Google's threat intelligence ensuring that new intelligence is being matched against newly ingested data as well as older data.
Supercharge productivity with generative AI
Use natural language to search your data, iterate, and drill down. Gemini generates underlying queries and presents full mapped syntax.
Investigate more efficiently with AI-generated summaries of what’s happening in cases, along with recommendations on how to respond.
Interact with Google Security Operations using a context-aware AI-powered chat, including the ability to create detections and playbooks.
Operate at Google scale and speed
Correlate petabytes of your telemetry and get actionable threat information with sub-second search.
Leverage Google Cloud’s planetary scale to quickly and securely ingest all relevant security telemetry.
Retain data for 12 months by default to enable retroactive matching of IoCs and threat hunting by your team or by Mandiant Experts.
Automatically parse log files to arm your security team with the right data and context and reduce the toil of parser creation and maintenance.
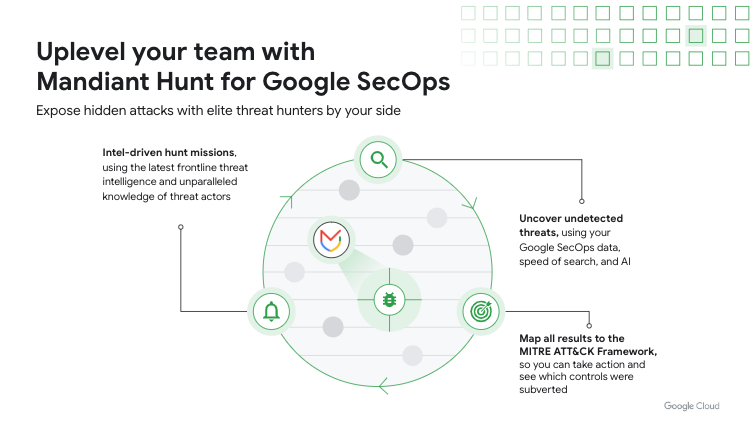
Augment your team with expert help
Partner with Mandiant elite threat hunters, leveraging advanced techniques, to hunt for hidden attackers seamlessly using your Google Security Operations data.
Get complete visibility and actionable insights into what our expert hunters looked for, how and where they looked, and what they found—mapped to the MITRE ATT&CK® framework.
How It Works
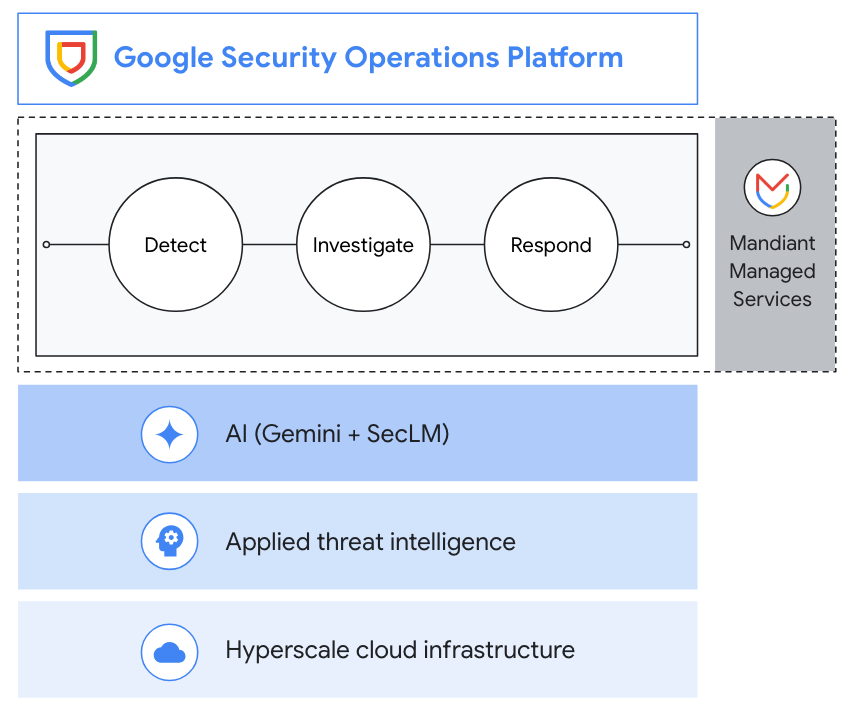
Google Security Operations offers a unified experience across SIEM, SOAR, and threat intelligence to drive better detection, investigation, and response. Collect security telemetry data, apply threat intel to identify high priority threats, drive response with playbook automation, case management, and collaboration.
Google Security Operations offers a unified experience across SIEM, SOAR, and threat intelligence to drive better detection, investigation, and response. Collect security telemetry data, apply threat intel to identify high priority threats, drive response with playbook automation, case management, and collaboration.
Common Uses
SOC modernization
Drive SOC modernization
Drive SOC modernization
Protect your organization against modern-day threats by transforming your security operations.
Tutorials, quickstarts, & labs
Drive SOC modernization
Drive SOC modernization
Protect your organization against modern-day threats by transforming your security operations.
SIEM augmentation
Eliminate blindspots and automate response
Eliminate blindspots and automate response
Enhance your organization’s threat detection, investigation, and response at a predictable cost with Google’s cloud-native hyperscale security operations platform.
Tutorials, quickstarts, & labs
Eliminate blindspots and automate response
Eliminate blindspots and automate response
Enhance your organization’s threat detection, investigation, and response at a predictable cost with Google’s cloud-native hyperscale security operations platform.
Google Cloud Cybershield™
Defend against threats at national scale
Defend against threats at national scale
Transform government security operations to provide cyber defense at national scale with tailored and applied threat intelligence, streamlined security operations, and capability excellence.
Tutorials, quickstarts, & labs
Defend against threats at national scale
Defend against threats at national scale
Transform government security operations to provide cyber defense at national scale with tailored and applied threat intelligence, streamlined security operations, and capability excellence.
Pricing
| About Google Security Operations pricing | Google Security Operations is available in packages and based on ingestion. Includes one year of security telemetry retention at no additional cost. | |
|---|---|---|
| Package type | Features included | Pricing |
Standard | Base SIEM and SOAR capabilities Includes the core capabilities for data ingestion, threat detection, investigation and response with 12 months hot data retention, full access to our 700+ parsers and 300+ SOAR integrations and 1 environment with remote agent. The detection engine for this package supports up to 1,000 single-event and 75 multi-event rules. Threat intelligence Bring your own threat intelligence feeds. | Contact sales for pricing |
Enterprise | Includes everything in the Standard package plus: Base SIEM and SOAR capabilities Expanded support to unlimited environments with remote agent and a detection engine that supports up to 2,000 single-event and 125 multi-event rules. UEBA Use YARA-L to create rules for your own user and entity behavior analytics, plus get a risk dashboard and out of the box user and entity behavior-style detections. Threat intelligence Adds curation of enriched open source intelligence that can be used for filtering, detections, investigation context and retro-hunts. Enriched open source intelligence includes Google Safe Browsing, remote access, Benign, and OSINT Threat Associations. Google curated detections Access out-of-the-box detections maintained by Google experts, covering on-prem and cloud threats. Gemini in security operations Take productivity to the next level with AI. Gemini in security operations provides natural language, an interactive investigation assistant, contextualized summaries, recommended response actions and detection and playbook creation. | Contact sales for pricing |
Enterprise Plus | Includes everything in the Enterprise package plus: Base SIEM and SOAR capabilities Expanded detection engine supporting up to 3,500 single-event rules and 200 multi-event rules. Applied threat intelligence Full access to Google Threat Intelligence (which includes Mandiant, VirusTotal, and Google threat intel) including intelligence gathered from active Mandiant incident response engagements. On top of the unique sources, Applied Threat Intelligence provides turnkey prioritization of IoC matches with ML-base prioritization that factors in each customer's unique environment. We will also go beyond IoCs to include TTPs in understanding how an adversary behaves and operates. Google curated detections Additional access to emerging threat detections based on Mandiant's primary research and frontline threats seen in active incident response engagements. BigQuery UDM storage Free storage for BigQuery exports for Google SecOps data up to your retention period (12 months by default). | Contact sales for pricing |
About Google Security Operations pricing
Google Security Operations is available in packages and based on ingestion. Includes one year of security telemetry retention at no additional cost.
Standard
Base SIEM and SOAR capabilities
Includes the core capabilities for data ingestion, threat detection, investigation and response with 12 months hot data retention, full access to our 700+ parsers and 300+ SOAR integrations and 1 environment with remote agent.
The detection engine for this package supports up to 1,000 single-event and 75 multi-event rules.
Threat intelligence
Bring your own threat intelligence feeds.
Contact sales for pricing
Enterprise
Includes everything in the Standard package plus:
Base SIEM and SOAR capabilities
Expanded support to unlimited environments with remote agent and a detection engine that supports up to 2,000 single-event and 125 multi-event rules.
UEBA
Use YARA-L to create rules for your own user and entity behavior analytics, plus get a risk dashboard and out of the box user and entity behavior-style detections.
Threat intelligence
Adds curation of enriched open source intelligence that can be used for filtering, detections, investigation context and retro-hunts. Enriched open source intelligence includes Google Safe Browsing, remote access, Benign, and OSINT Threat Associations.
Google curated detections
Access out-of-the-box detections maintained by Google experts, covering on-prem and cloud threats.
Gemini in security operations
Take productivity to the next level with AI. Gemini in security operations provides natural language, an interactive investigation assistant, contextualized summaries, recommended response actions and detection and playbook creation.
Contact sales for pricing
Enterprise Plus
Includes everything in the Enterprise package plus:
Base SIEM and SOAR capabilities
Expanded detection engine supporting up to 3,500 single-event rules and 200 multi-event rules.
Applied threat intelligence
Full access to Google Threat Intelligence (which includes Mandiant, VirusTotal, and Google threat intel) including intelligence gathered from active Mandiant incident response engagements.
On top of the unique sources, Applied Threat Intelligence provides turnkey prioritization of IoC matches with ML-base prioritization that factors in each customer's unique environment. We will also go beyond IoCs to include TTPs in understanding how an adversary behaves and operates.
Google curated detections
Additional access to emerging threat detections based on Mandiant's primary research and frontline threats seen in active incident response engagements.
BigQuery UDM storage
Free storage for BigQuery exports for Google SecOps data up to your retention period (12 months by default).
Contact sales for pricing
Get a demo
The Business Value of Google SecOps
Learn what Google Security Operations can do for you
"Our SOC and analysts are able to prioritize work and respond with the attention that is needed"
"[Google SecOps] is a robust platform that allows customers to ingest any kind of data at volume"
Join the Google Cloud Security community
Learn the technical aspects of Google Security Operations
New to Google Security Operations?
Business Case
Explore how organizations like yours cut costs, increase ROI, and drive innovation with Google Security Operations
IDC Study: Customers cite 407% ROI with Google Security Operations
CISO, multi-billion dollar automotive company
"Our cybersecurity teams deal with issues faster with Google Security Operations, but they also identify more issues. The real question is, 'how much safer do I feel as a CISO with Google Security Operations versus my old platform?' and I would say 100 times safer."
Read the studyTrusted and loved by security teams around the world
"We can now use natural language search to query large amounts of data which we estimate will improve our ability to transform, synthesize, and make data meaningful by 10X." - Dennis McDonald, CISO, Jack Henry
"We have advanced capabilities around threat intelligence that are highly integrated into the Google Security Operations platform. We like the orchestration capabilities that enable us to enrich the data and provide additional context to it, so our SOC and analysts are able to prioritize that work and respond with the attention that is needed." - Bashar Abouseido, CISO, Charles Schwab
"When we moved to Google Security Operations, we were able to reduce the time to detect and time to investigate from 2 hours to about 15 to 30 minutes. No longer spending time in disparate tools but performing the job functions of a security operations analyst, it empowers them to work on more advanced workflows." - Hector Peña, Senior Director of Information Security, Apex FinTech Solutions
FAQ
Is Google Security Operations only relevant for Google Cloud?
No. Google SecOps ingests and analyzes security telemetry from across your environment, including on-premises and all major cloud providers, to help you detect, investigate and respond to cyberthreats across your organization. Check out the complete list of supported log types and parsers.
Can I bring my own threat intelligence feeds to Google Security Operations?
Yes. You can integrate any threat intelligence feeds with Google SecOps. Note that the automatic application of threat intelligence for threat detection is only supported for Google’s threat intelligence feeds.
Does Google Security Operations support data residency for specific regions?
Yes. The full list of available regions can be found here.