Inspect view: "View on IPFS Gateway" still points to the ip-address, not to .localhost #1490
Labels
effort/hours
Estimated to take one or several hours
exp/intermediate
Prior experience is likely helpful
kind/bug
A bug in existing code (including security flaws)
P1
High: Likely tackled by core team if no one steps up
status/ready
Ready to be worked
Milestone
Describe the bug
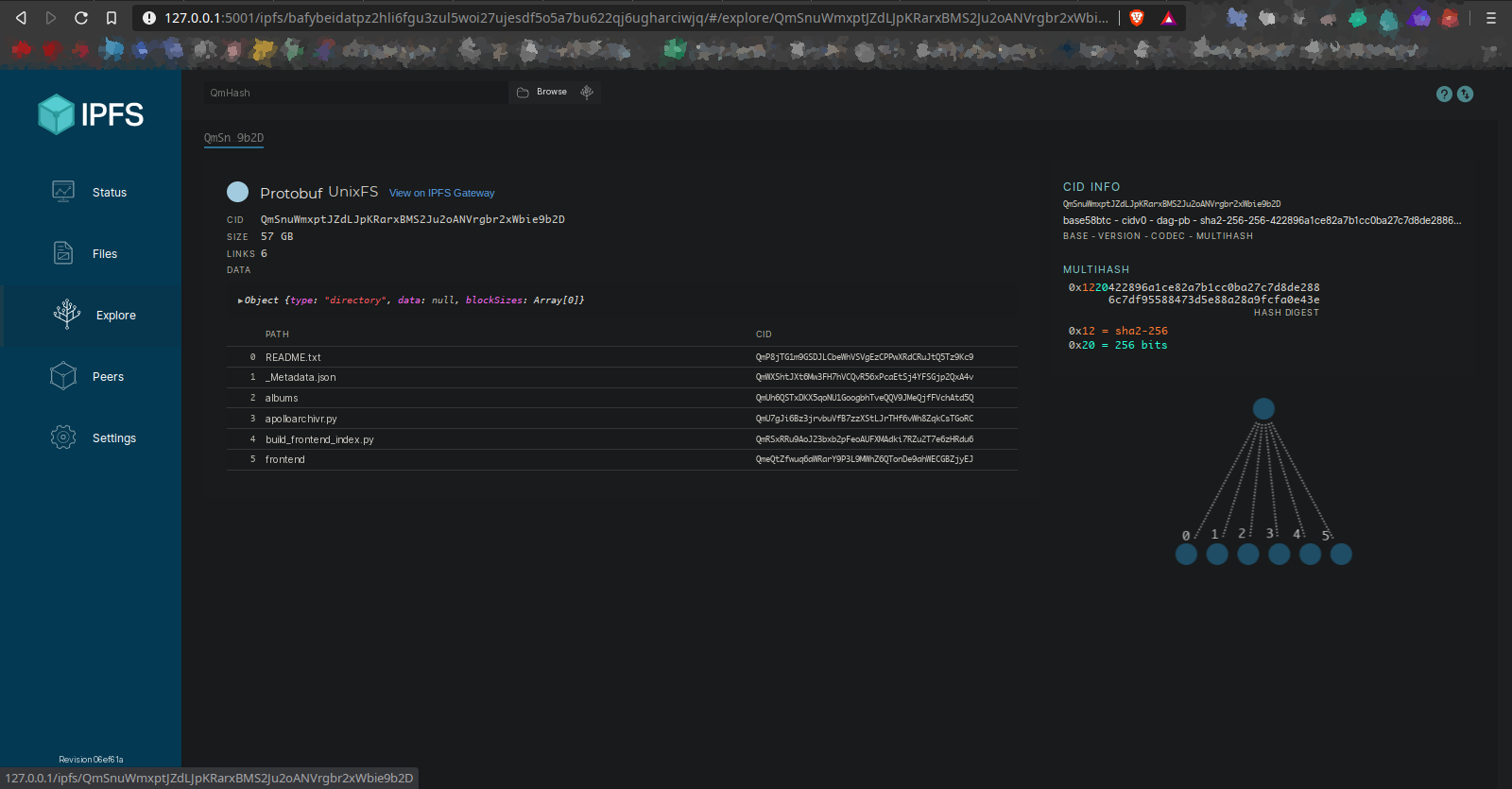
On the inspect view there's a button labled with "View on IPFS Gateway", which still points (in my case) to
127.0.0.1/ipfs/<CID>instead of<CID>.ipfs.localhost.Screenshots
Desktop (please complete the following information):
The text was updated successfully, but these errors were encountered: